Security came first in every step of building Euler v2.
The vision for transitioning Euler into a modular protocol dates back to 2022. Since then, various code designs have been explored as proof of concepts long before work officially began on what will be launched in the very near future.
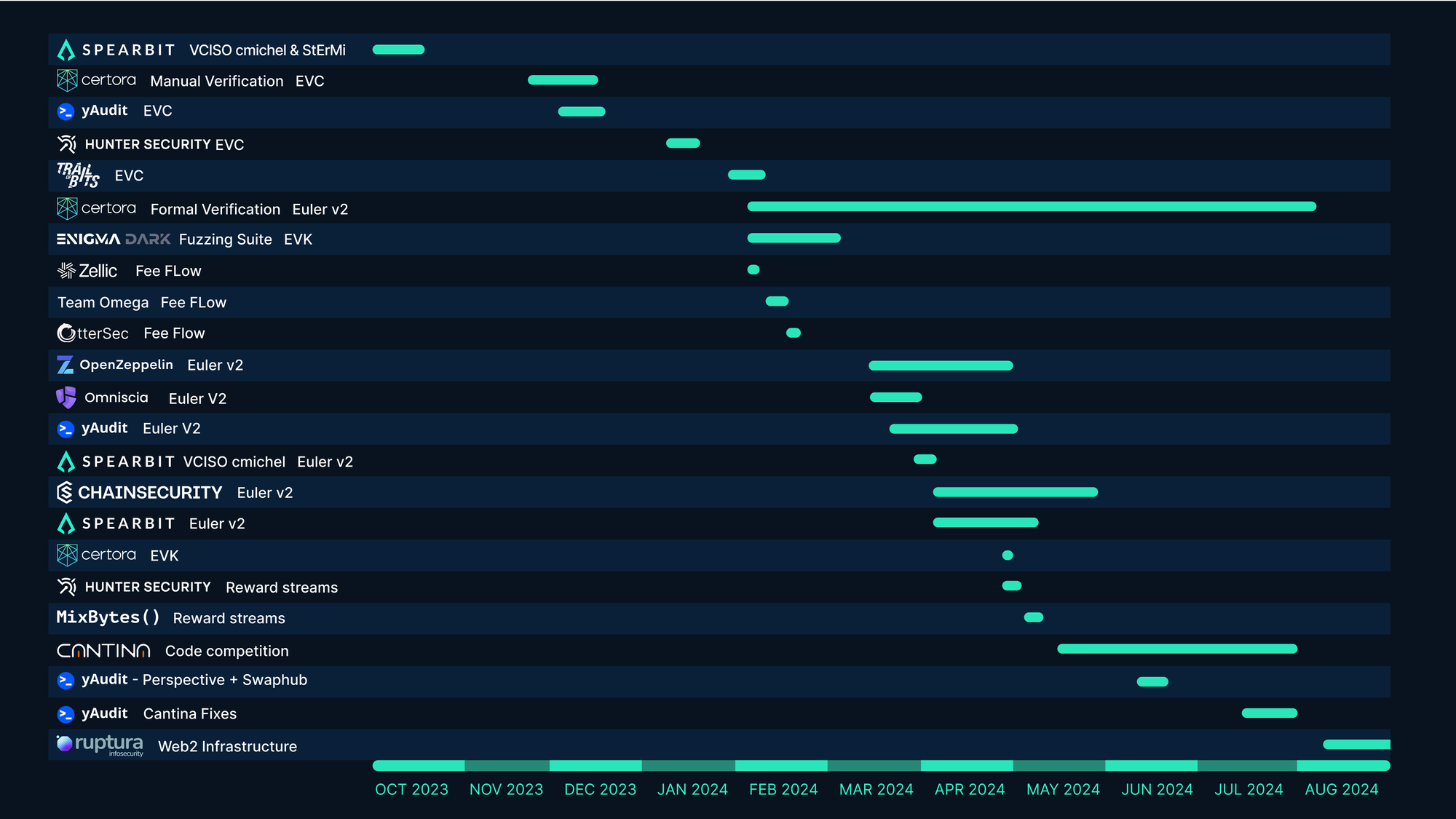
As we head toward that milestone, we’re proud to share today that Euler v2 has undergone one of the most expensive and comprehensive security processes for any DeFi protocol to-date. Roughly $4m was allocated by Euler DAO to security — an incredible budget for an app-layer protocol, with many protocols budgeting closer to low six figures. Those costs covered the hiring of a dedicated Senior Cybersecurity Engineer to oversee development processes, engagements with world-class security researchers early in protocol development, the creation of bespoke fuzz testing and formal verification testing suites, 31 audits from 13 different firms, all culminating in the largest ever ($1.25m) code audit competition.
We draw inspiration from Morpho’s excellent framework on the same topic. Note that we have limited the content to only the key processes in the development of the smart contracts, but this is only one part of a bigger picture covering the security of Euler.
Reinforcing Security Through Modularity
The primary goal of Euler v2's modular design was to improve the security and risk management of the protocol. We believe modularity is the way forward for protocol development because it can lead to more secure software that isolates risk, is easier to test, analyze, and audit, and reduces single points of failure. The core modules in Euler v2 are designed to do a small number of things in a very well-specified way. These modules include:
- Ethereum Vault Connector (EVC)
- Euler Vault Kit (EVK)
- Euler Price Oracle (EPO)
The audit process detailed later in this blog post highlights the key benefits of Euler v2’s modular design, which enabled internal and external teams to develop and test modules both in isolation and in composition with other modules.
Security-first processes
While it is common to develop a protocol and later bring in auditors to consider its security after it has been developed, Euler v2 development turned this process upside down.
With the goal of implementing the “Swiss Cheese” model of security for v2, Euler DAO allocated roughly $4m to security — an incredible budget for a DeFi protocol, with many protocols budgeting low six figures. This capital allowed us to bring in world-class protocol engineers and security researchers early on during the design and proof-of-concept stages of Euler’s development.
To oversee processes and operations for security, Erik Arfvidson was hired by Euler Labs as Head of Security. Erik has over 16 years of experience in security, spanning web2 and web3. In addition to managing day-to-day security operations and working closely with external security partners, Erik has been working to ensure that all development practices at Euler are compliant with ISO27001 standards, which is a certification standard used by banks and defense companies.
At the onset, we engaged:
- Certora to bring two security engineers in-house for six months to help guide development and formally prove assumptions about code operations;
- Alberto Cuesta Cañada, ERC-4626 pioneer and developer of Yield protocol, to challenge the structure behind v2 and helped dive deep into thorny attack vectors for lending protocols. This work led to our publishing of an article on exchange rate manipulation of lending protocols; and
- Cmichel and StErMi, leading security engineers from Spearbit and experts in lending protocol attack vectors, to come in-house to challenge the designs behind the protocol’s architecture, carry out threat modeling, and help conduct line-by-line analysis of key parts of the early codebase.
Testing, fuzz testing and formal verification
As the protocol began to take shape, a comprehensive suite of unit and invariant tests were also developed alongside Euler v2. Enigma Dark’s Victor Martinez was hired to build a dedicated fuzz testing suite using Medusa and Echidna, while Certora helped build a formal verification testing suite.
These two methodologies are important complementary tools for testing protocol invariants and finding edge cases in which, despite best efforts, unexpected things happen in a protocol’s code. Fuzz testing bombards a protocol’s code with randomness to find when key assumptions might be broken. Formal verification turns the codebase into a system of equations and helps formally prove that certain invariants cannot ever be broken. Fuzz testing is generally more flexible to apply but cannot prove things, while formal verification is harder to use in all cases but provides formal proofs when it works.
One of the most important invariants a lending protocol needs to test is that a user’s health should not change unless their balances or the prices of the assets they hold do. Breaking this invariant, or proving it couldn’t be broken, was set as a key challenge for both invariant testing suites. Formally proving that it couldn’t be broken was considered a ‘Holy grail’ for formal verification, which is something Certora’s team, with significant contributions from Andrew Ferraiuolo, duly delivered on (see below).
Internal and external audits
Once each module of Euler v2 was completed, it was manually audited both internally (within Euler Labs) and externally (by leading web3 security firms). Euler Labs is fortunate to house multiple smart contract teams, each of which can be used to audit another team’s code once it is completed prior to it being sent out to an external firm. To date, 29 external audits by 12 different firms have been carried out on the Euler v2 codebase.
The audit process for Euler v2 highlights a key benefit of its modular design. Each module in Euler is designed to do a few things in a very well-specified way, which allows for better documentation of assumptions about what the code should do and ultimately makes things easier for auditors. In particular, it allows for independent teams to develop and test modules both in isolation and in composition with other modules.
Utilising multiple audit firms allowed world-class security researchers with diverse backgrounds to bring their domain expertise to designing and battle testing the codebase. This helped to break ground on new areas of research, especially technical issues, such as those surrounding Dutch-auction-style liquidations.
Euler was audited by the world’s best web3 security firms.
Coordinating the Largest Code Audit Competition Ever
Code audit competitions have emerged as an essential part of the auditing pipeline, which go beyond manual reviews and formal audit engagements by experts to crowdsource security to the general public. This style of auditing is highly complementary to formal auditing processes as it invites a far more diverse cross-section of candidates to challenge a codebase using whatever experience and techniques they have at their disposal.
Cantina was therefore engaged to carry out the world’s largest ever* code audit competitions on the Euler v2 codebase with $1.25m allocated to security researchers who could find any additional post-audit bugs. The largest prize was for issues with High severity. The contest went viral, with more than 600 participants worldwide participating and, in some cases, live blogging about their attempts to claim the top prize.
Ultimately, no high or medium severity issues were found in the post-audit code (see Appendix for severity definitions), which is almost unheard of in contests of this scale. Despite this, we awarded researchers by allocating $200k for low issues found, as a way of thanking the security community for all of their hard work and contribution.
*Other projects have since followed Euler’s trend and hosted even larger competitions.
The Ultimate Security Test
While audits and code competitions are crucial for identifying bugs and potential attack vectors, they also have some inherent limitations as they primarily focus on static analysis and testing within controlled environments rather than testing the active defence and security of live contracts.
To put to the test all of the security efforts we had done until this point, we wanted to take a more direct approach by depositing funds into live contracts and inviting whitehats to attempt to retrieve those funds with no bug submissions being required.
In collaboration with Hats Finance, we launched a Capture The Flag with ~$3.5 million on the line. On August 20th, funds were deposited into Euler’s USDC/ETH and WETH/USDC pools and on August 21st participants could attempt to retrieve any funds they could while simultaneously testing our active defences. 13 days later, on September 2nd, no one managed to extract any funds, leaving Euler v2's contracts uncracked as the challenge concluded.
Conclusion
To summarise, Euler v2 has been secured by experienced security professionals who have monitored and shaped its development from start to finish, from its modular design to line-by-line code reviews.
It is crucial to note, however, that security does not stop with audits and is not limited to securing a protocol’s smart contracts only. The work highlighted here is only part of a much bigger security picture for the protocol. This article has not touched on countless other security initiatives that help secure the protocol, including bug bounties, monitoring, penetration tests for the user interface, plans for critical incidents, and much else.
When it comes to security, there is always more to be done.
This content is brought to you by Euler Labs, which wants you to know a few important things.
This piece is provided by Euler Labs Ltd. for informational purposes only and should not be interpreted as investment, tax, legal, insurance, or business advice. Euler Labs Ltd. and The Euler Foundation are independent entities.
Neither Euler Labs Ltd., The Euler Foundation, nor any of their owners, members, directors, officers, employees, agents, independent contractors, or affiliates are registered as an investment advisor, broker-dealer, futures commission merchant, or commodity trading advisor or are members of any self-regulatory organization.
The information provided herein is not intended to be, and should not be construed in any manner whatsoever, as personalized advice or advice tailored to the needs of any specific person. Nothing on the Website should be construed as an offer to sell, a solicitation of an offer to buy, or a recommendation for any asset or transaction.
This post reflects the current opinions of the authors and is not made on behalf of Euler Labs, The Euler Foundation, or their affiliates and does not necessarily reflect the opinions of Euler Labs, The Euler Foundation, their affiliates, or individuals associated with Euler Labs or The Euler Foundation.
Euler Labs Ltd. and The Euler Foundation do not represent or speak for or on behalf of the users of Euler Finance. The commentary and opinions provided by Euler Labs Ltd. or The Euler Foundation are for general informational purposes only, are provided "AS IS," and without any warranty of any kind. To the best of our knowledge and belief, all information contained herein is accurate and reliable and has been obtained from public sources believed to be accurate and reliable at the time of publication.
The information provided is presented only as of the date published or indicated and may be superseded by subsequent events or for other reasons. As events and markets change continuously, previously published information and data may not be current and should not be relied upon.
The opinions reflected herein are subject to change without being updated.